
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment, and resources and to protect personnel and property from damage or harm such as espionage, theft, or terrorist attacks. Physical security involves the use of multiple layers of interdependent systems that can include CCTV surveillance, security guards, protective barriers, locks, access control, perimeter intrusion detection, deterrent systems, fire protection, and other systems designed to protect persons and property. Deterrence physical security measures are focused on keeping introducers out of the secured area. Common methods include tall perimeter fences, barbed wire, clear signs stating that the sites have active security, commercial video cameras, and access controls. Detection works to catch any intruders if they manage to get past the deterrence measures. Within the four main types of physical security control categories deter, detect, delay, and respond is an enormous range of physical security tools and cutting-edge technology. Physical security technologies have evolved in leaps and bounds in recent years, offering advanced protection at accessible price points. Physical security devices now use cloud technology and artificial intelligence for even smarter real-time processing. Automated physical security components can perform several different functions in physical security systems.
Physical security technologies can log large quantities of data around the clock. Analytics powered by artificial intelligence can process all this data and provide helpful digests for the security team, saving valuable time and helping to make faster, better-informed decisions. Physical security is fundamental to business success. With the right physical security measures, it need not be expensive or difficult to maintain. The best way to guarantee a safe and secure workplace is to observe exactly what the company needs carefully and then find the right physical security tools, technology, and methods for the job.
Global Physical Security Market – Competitive Landscape
On May 17, 2023, in Austin, Texas, and Bethesda, Eagle Eye Networks and Brivo announced one of the largest investments to date in cloud physical security as Japan-based security integration company SECOM CO. LTD has made a primary equity investment of USD 192 million in two companies. On July 25, 2023, Solink a physical security company for businesses announced that it has closed USD 60 million in a series C investment round. SECOM made a USD 192 million investment in cloud physical security providers Eagle Eye and Brivo.
Some of the Key Players in the Global Physical Security Market Include –
Global Physical Security Market – Growth Driver
The integration of cutting-edge technologies, such as AI-driven surveillance systems, biometrics, and IoT-enabled devices, is a significant driver for the growth of the global physical security market. Escalating security threats, both physical and cyber, across various industries and regions, are fueling the demand for advanced physical security solutions to safeguard assets, data, and individuals. Governments worldwide are allocating substantial budgets for enhancing public safety, border control, and critical infrastructure protection, contributing significantly to the growth of the physical security sector. A heightened awareness of the importance of robust security measures is prompting organizations and individuals to invest in comprehensive physical security solutions, further driving market expansion. Sectors like transportation, healthcare, and finance are experiencing a surge in demand for tailored physical security solutions, creating specific growth pockets within the overall market. The ongoing trends of globalization and urbanization are amplifying the need for sophisticated security systems to address the unique challenges posed by densely populated urban areas and interconnected global networks.
Global Physical Security Market – Restraints
The implementation of sophisticated physical security measures often involves substantial upfront costs, acting as a significant barrier that hinders the growth of the physical security market. Integrating diverse security technologies and systems can be complex, leading to interoperability issues and hindering the seamless operation of a comprehensive physical security infrastructure. The development of advanced surveillance technologies raises concerns about individual privacy, leading to regulatory privacy, leading to regulatory challenges, and potential resistance from the public. Rapid advancements in technology may render existing physical security solutions obsolete, requiring continuous investments to stay ahead and maintain effective security measures. A shortage of skilled professionals capable of managing and maintaining complex security systems poses a challenge, limiting the optimal utilization of advanced physical security technologies. Evolving and stringent regulations related to data protection and security standards can pose challenges for organizations aiming to navigate and comply with diverse global requirements. According to security intelligence, the average cost for organizations that fail to comply with data protection regulations is USD 14.82 million.
Global Physical Security Market – Opportunity
The increasing focus on creating smart cities globally presents a significant opportunity for the physical security market, with a demand for integrated and intelligent security solutions to enhance urban safety. The proliferation of Internet of Things devices and connectivity provides opportunities for advanced sensor networks and real-time data analysis, improving the effectiveness of physical security measures. Heightened security concerns surrounding global events and critical infrastructure create opportunities for the development and implementation of tailored physical security solutions.
Global Physical Security Market – Geographical Insight
the market for global physical security is segmented into regions such as North America, Latin America, Asia-Pacific, Europe, the Middle East & Africa. North America is the largest region for the global physical security market due to its high awareness, significant investments in security infrastructure, and a strong focus on critical infrastructure protection. Asia-Pacific represents a rapidly growing market due to increasing urbanization, rising security concerns, and government initiatives to modernize security infrastructure. China and India are key contributors to this growth. European countries exhibit a robust adoption of physical security solutions, with an emphasis on integrated systems. A strict regulatory framework also contributes to the growth of the market in this region.
Global Physical Security Market – Key Development
Research Methodology: Aspects
Market research is a crucial tool for organizations aiming to navigate the dynamic landscape of customer preferences, business trends, and competitive landscapes. At Cognizance Market Research, acknowledging the importance of robust research methodologies is vital to delivering actionable insights to our clientele. The significance of such methodologies lies in their capability to offer clarity in complexity, guiding strategic management with realistic evidence rather than speculation. Our clientele seek insights that excel superficial observations, reaching deep into the details of consumer behaviours, market dynamics, and evolving opportunities. These insights serve as the basis upon which businesses craft tailored approaches, optimize product offerings, and gain a competitive edge in an ever-growing marketplace.
The frequency of information updates is a cornerstone of our commitment to providing timely, relevant, and accurate insights. Cognizance Market Research adheres to a rigorous schedule of data collection, analysis, and distribution to ensure that our reports reflect the most current market realities. This proactive approach enables our clients to stay ahead of the curve, capitalize on emerging trends, and mitigate risks associated with outdated information.
Our research process is characterized by meticulous attention to detail and methodological rigor. It begins with a comprehensive understanding of client objectives, industry dynamics, and research scope. Leveraging a combination of primary and secondary research methodologies, we gather data from diverse sources including surveys, interviews, industry reports, and proprietary databases. Rigorous data analysis techniques are then employed to derive meaningful insights, identify patterns, and uncover actionable recommendations. Throughout the process, we remain vigilant in upholding the highest standards of data integrity, ensuring that our findings are robust, reliable, and actionable.
Key phases involved in in our research process are mentioned below:

Understanding Clients’ Objectives:
Extensive Discussions and Consultations:
Industry and Market Segment Analysis:
Target Audience Understanding:
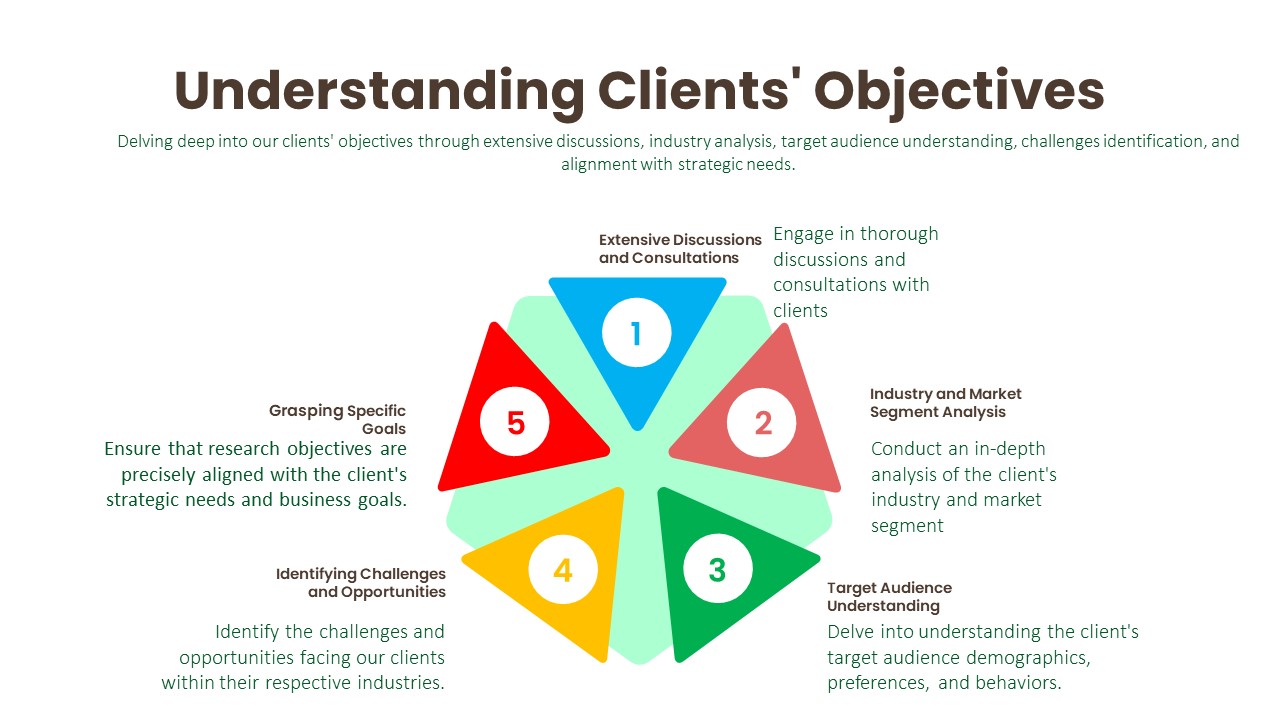
Identifying Challenges and Opportunities:
Grasping Specific Goals:
Data Collection:
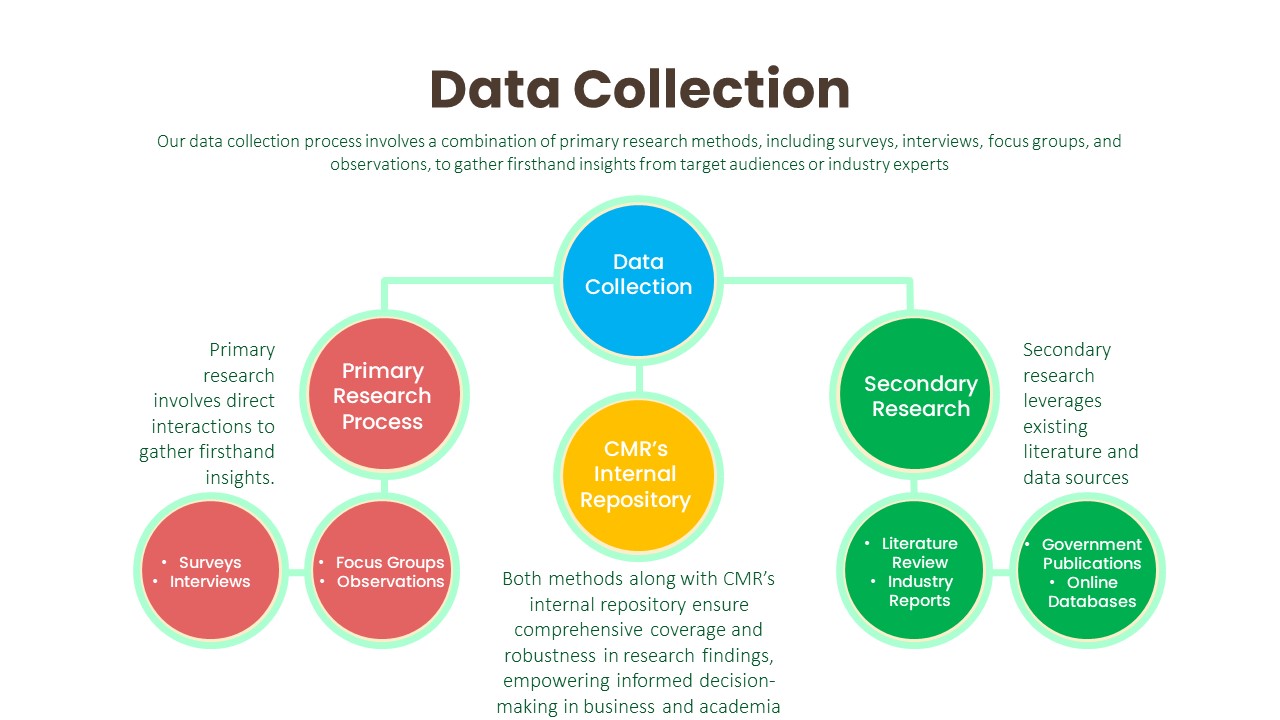
Primary Research Process:
Secondary Research Process:

Data Analysis:
The data analysis phase serves as a critical juncture where raw data is transformed into actionable insights that inform strategic decision-making. Through the utilization of analytical methods such as statistical analysis and qualitative techniques like thematic coding, we uncover patterns, correlations, and trends within the data. By ensuring the integrity and validity of our findings, we strive to provide clients with accurate and reliable insights that accurately reflect the realities of the market landscape.

Transformation of Raw Data:
Utilization of Analytical Methods:
Statistical Analysis:
Qualitative Analysis Techniques:
Integrity and Validity Maintenance:
Data Validation:
The final phase of our research methodology is data validation, which is essential for ensuring the reliability and credibility of our findings. Validation involves scrutinizing the collected data to identify any inconsistencies, errors, or biases that may have crept in during the research process. We employ various validation techniques, including cross-referencing data from multiple sources, conducting validity checks on survey instruments, and seeking feedback from independent experts or peer reviewers. Additionally, we leverage internal quality assurance protocols to verify the accuracy and integrity of our analysis. By subjecting our findings to rigorous validation procedures, we instill confidence in our clients that the insights they receive are robust, reliable, and trustworthy.
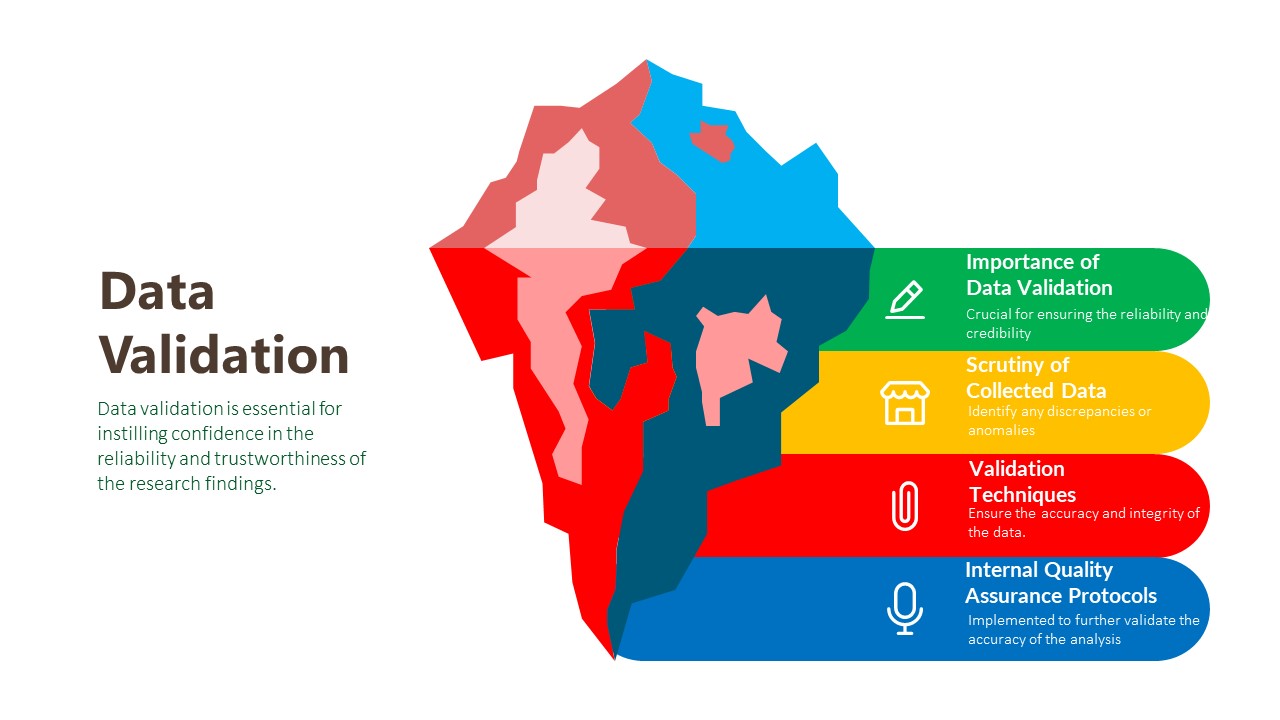
Importance of Data Validation:
Scrutiny of Collected Data:
Validation Techniques:
Internal Quality Assurance Protocols:
We can customize every report – free of charge – including purchasing stand-alone sections or country-level reports
We help clients to procure the report or sections of the report at their budgeted price. Kindly click on the below to avail
Cognizance market research is continuously guiding customers around the globe towards strategies for transformational growth. Today, businesses have to innovate more than ever before, not just to survive, but to succeed in the future

© 2023 All rights Reserved. Cognizance Market Research